General information
- malware name: ElectroRAT
- hash: 2a3b92f6180367306d750e59c9b6446b
1. Sandbox output
- Sandbox: ANY.RUN
- Link: https://app.any.run/tasks/c40b44a1-0f8a-4c76-86b4-d6728e28ee34
2. Basic PE inspection
Overview
Let’s do a static analysis of the sample. We start with Detect It Easy showing us the following output:
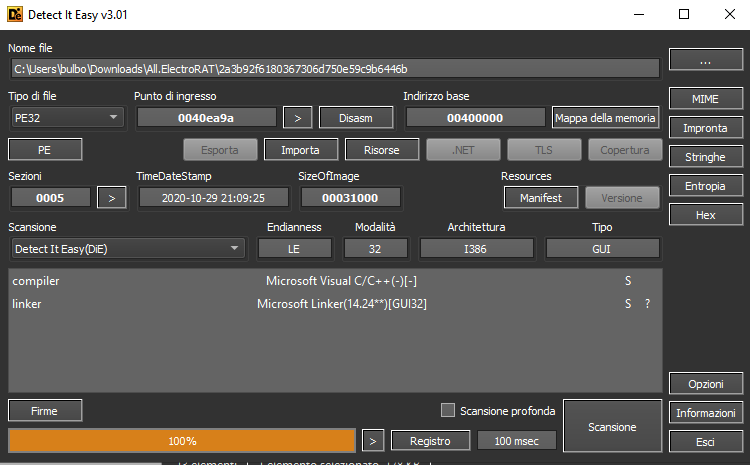 It reveals a C++ writter malware using Microsoft Linker. We also see some calls to set
It reveals a C++ writter malware using Microsoft Linker. We also see some calls to set security_cookie, typically of Visual Studio compiler. From the entropy menu we get that the global entropy is under the threshold, so the sample might not be packed:
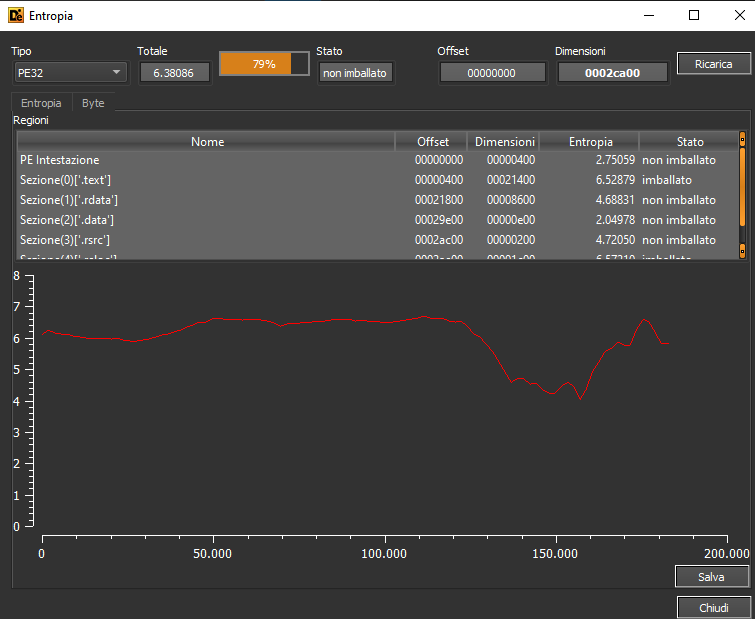
Sections
From PE Studio we have another indicator that the malware is not packed, since there’s no huge difference between virtual size and raw size
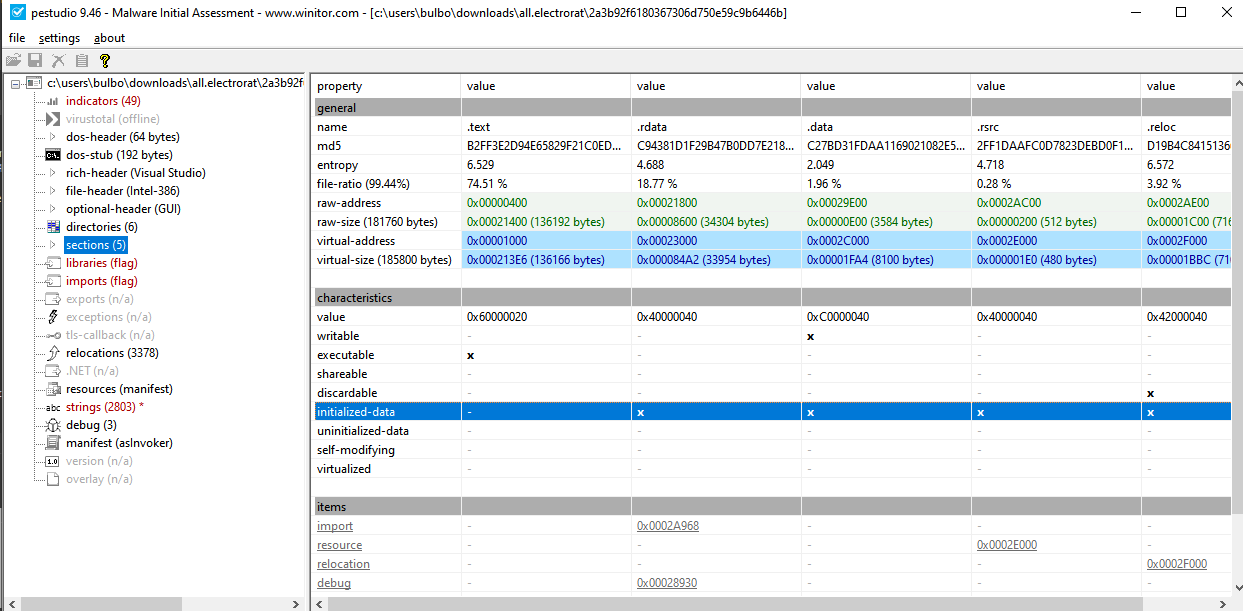
Imports
All the imports flags as suspicious by PEStudio are those:
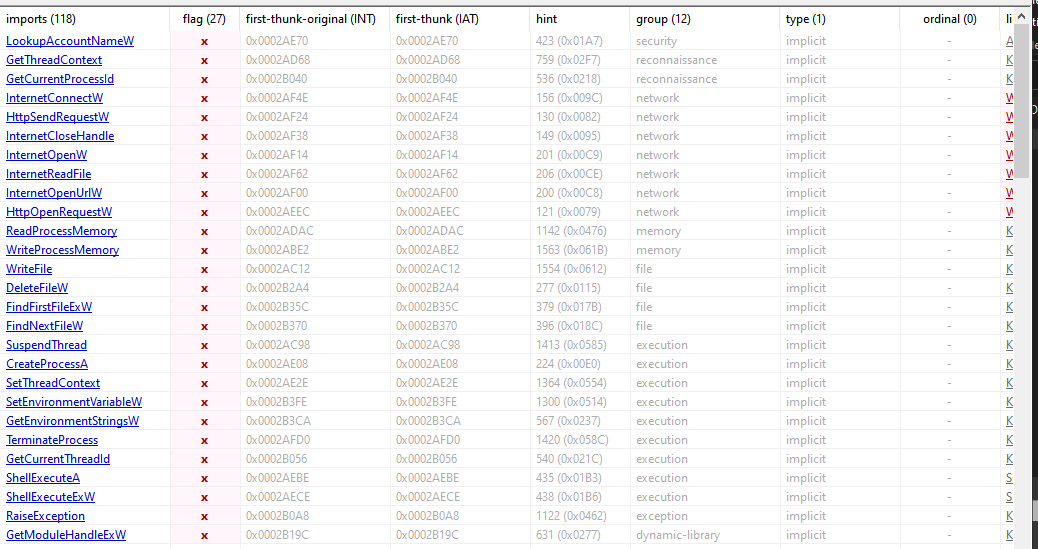 Generally, we can assume already 3 activities done by malware:
Generally, we can assume already 3 activities done by malware:
- IAT function hiding: here,
GetModuleHandle[Ex]WandGetProcAddressare used to dynamically solve the imports so they don’t show in a static analysis tool - Connecting back to rogue server:
InternetOpenW,InternetReadFile,InternetCloseHandle,InternetOpenUrlW,HttpOpenRequestW,HttpSendRequestWet similia should be investigated to actually understand what is sent and possibly what is received - Injection:
GetThreadContext,SetThreadContext,SuspendThread,ResumeThread,WriteProcessMemoryare good candidates to some process injection
Strings
We highlight the most relevant strings found:
D:\Mktmp\NL1\Release\NL1.pdb: nothing particular, but the pdb path could possibly leak the usernameNL1that can be used as an IOC for the threat actor name!"#$%&'()*+,-./0123456789:;<=>?@abcdefghijklmnopqrstuvwxyz[\]^_``abcdefghijklmnopqrstuvwxyz{|}~: alphabets may indicate that there is some obfuscation method used inside the logicAVAST Software,Avira,Kaspersky Lab,ESET,Panda Security,Doctor Web,AVG,360TotalSecurity,Bitdefender,Norton,Sophos,Comodo: all these strings might be used for comparison when scanning for AV software present in the system
Resources
ResourceHacker reveals no resources embedded inside the malware.
3. High-level description of the sample
Description
At the start, malware spawns different threads each one doing with a specific task.
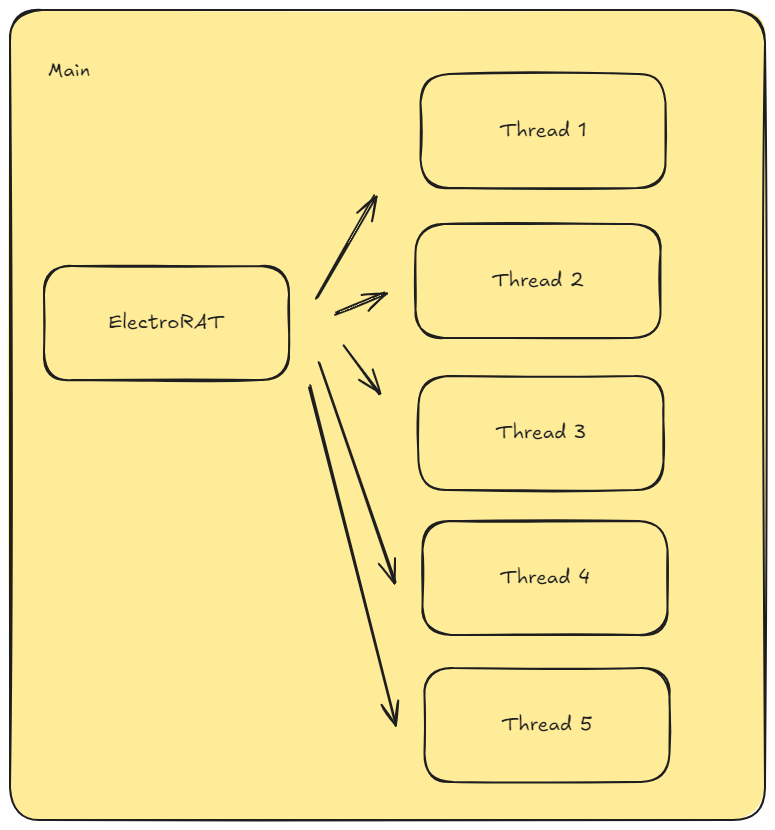 This malware implement the most basic activities of a RAT. There’s info extraction through
This malware implement the most basic activities of a RAT. There’s info extraction through GetUsernameW and other Win APIs, network activity through DNS, persistence and not-so-sophisticated evasion mechanisms.
Evasion mechanisms
Malware tries remove a local proxy probably to contact outside websites when doing network activity. It does that by setting some proxy reg keys inside the path HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap.
Also, scanning software is checked by malware before revealing its malicious activities.
Persistence
Malware puts itself inside Windows managed tasks. It accomplishes that using schtasks.exe, the Windows Task Scheduler service.
Files and registry activity
The following list includes the registry keys touched by malware
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap:ProxyBypass=1HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap:UNCAsIntranet=1HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap:IntranetName=1