Challenge
Challenge presents as a Python-compiled executable. If we run the exe a simple GUI with a prompt is shown:
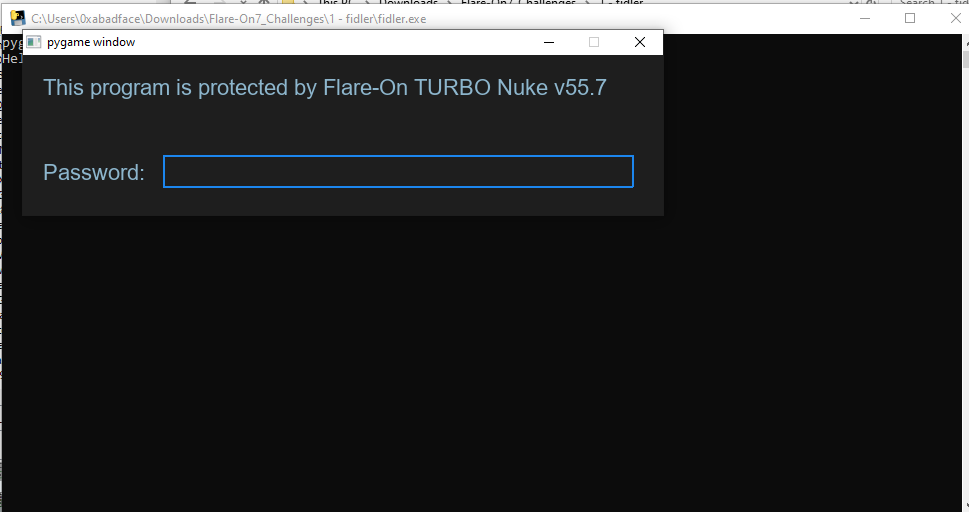
We need to go further into the solution to discuss the details of this challenge.
Solution
By checking with Detect It Easy the executable has been compiled with PyInstaller, a tool to transform python scripts into PE files. We can easily see through the .py code the logic that does the password checking:
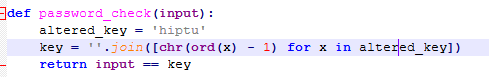 The key
The key hiptu is reordered by decrement each character ascii value by 0x1. So:
h⇒gi⇒hp⇒ot⇒su⇒t
We prompt ghost and a new window is shown:
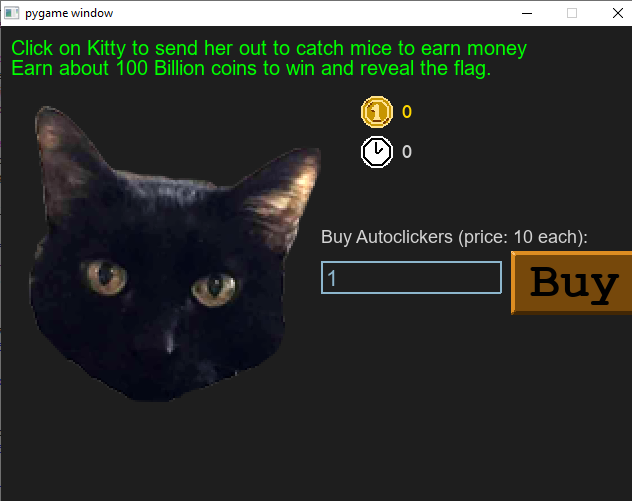
Ok, we can just play the game, clicking mouse and also buying autoclickers but I don’t have time since I ordered a pizza 1h ago and it’ll come in 5 minutes!
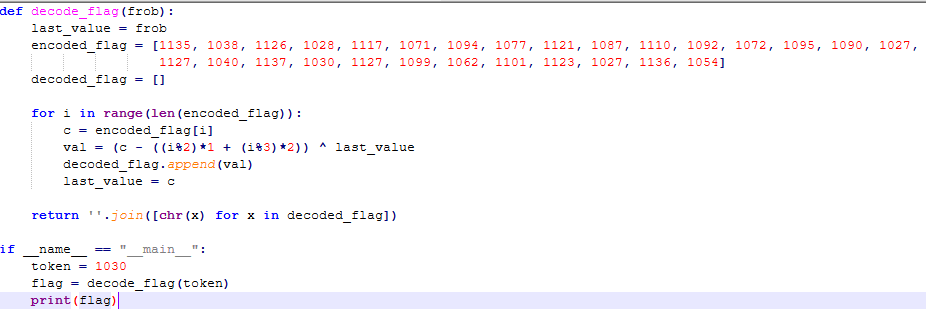
Let’s do this quickly! Inside the same python script there’s also the decoding logic of the flag:
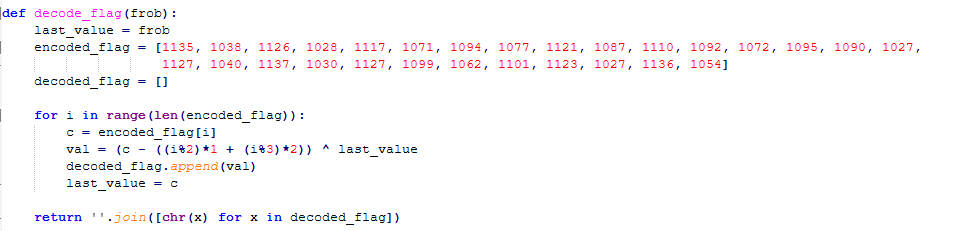
Ok, so decode_flag receives a frob parameter that somewhere must be retrieved/calculated. A quick search reveals that victory_screen(int(current_coins / 10**8)) calls decode_flag() passing its initial parameter:
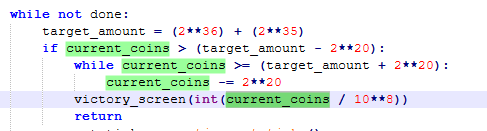
Calculator on the other hand and the parameter passed inside victory_screen is 1030. We input this parameter to our script:
 and…
and…
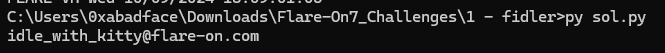
Bye, I have a pizza to eat!
